College of the Desert paid $1.1M to hackers in 2020 ransomware attack, doing more now to cyber safeguard its IT systems
An I-Team investigation reveals College of the Desert paid more than a million dollars in digital ransom to recover data after a 2020 malware attack.
And as KESQ News Channel 3 has extensively reported the college suffered another malware attack this past summer.
That second July attack may have compromised the personal data of hundreds of people connected to the college.
I-Team investigator Jeff Stahl reviewed years of records to examine the weaknesses found and the improvements being made to better cyber safeguard the campus IT systems.
While College of the Desert says it’s doing more now than ever before to prevent a future malware attack, its board of trustees still calls the school’s IT systems “vulnerable” and “inefficient.”

The college was subjected to a crippling ransomware attack in August 2020 under former COD President Joel Kinnamon. The I-Team obtained the school’s timeline of that hack. It indicates the school paid three ransom payments in Bitcoin to three or more attackers totaling $1,145,000 million dollars. The money was paid by an insurance company and resulted in the restoration of encrypted databases.
A fact-finding report at the time noted some of the college’s previously identified obsolete servers had never been replaced “even though there were technology replacement funds available.”
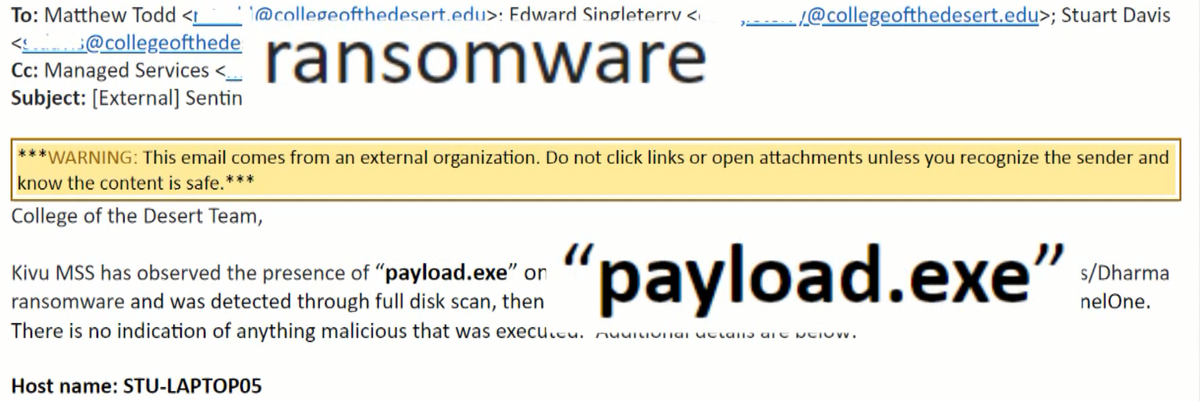
Emails the I-team obtained from the college show IT workers also noted a campus computer infected with ransomware last May. That machine quarantined the malicious file, which was never executed.
In March of 2022, the school, using a contractor, identified dozens of security weaknesses and vulnerabilities in its IT systems including obsolete and unsupported operating database servers. Some were operating with Windows 2008, utilizing weak encryption protocols. At the time, emails indicated the school’s tech team said those servers were being replaced.
It took nearly a month for all of College of the Desert’s online student services to be restored following a second damaging July 5, 2022 malware attack.
Administrators called in the FBI to investigate. The school denied our I-Team request to see those communications.
In early March of 2023, COD announced the personal information of up to 800 people might have been accessed without authorization.

Jeff Stahl asked, “It was a seven-month span. Why did it take so long?” Kristeen Farlow, COD Interim Public Information Officer replied, “We notified as soon as we could as soon as we had solid information about the number of accounts and the potential information that was at risk from this malware attack.”
We contacted a cyber security expert who agreed that seven months is likely reasonable to announce the results of a deep forensic investigation.
“They may not have been able to issue the warning sooner. Whether or not it was a reasonable amount of time is a hard question to answer.”
Nick Lumsden, NYJL Advisors
Jeff Stahl asked Nick Lumsden of NYJL Advisors, “Should they have issued this warning sooner?” Lumsden, an online security consultant replied, “They may not have been able to issue the warning sooner. Whether or not it was a reasonable amount of time is a hard question to answer.”
Lumsden says some malware investigations often take more than a year to complete. “It can take a long time to do the forensics,” Lumsden said.
The college initiated a lengthy investigative process with local authorities, the FBI, as well as forensic cybersecurity specialists, according to Farlow. “It was a very lengthy in-depth process for them to cull through the information in the files and assess really what was accessed rather than saying it was our entire system,” Farlow said.
“If I were COD, I would understand the anatomy of those attacks,” said Lumsden adding, “and make a very intentional investment in making sure those attacks never happen again.”
The college says its tech staff is working hard to mitigate and implement new systems and procedures to prevent another attack or make any intrusion less invasive. There are no guarantees, however. “We can’t say— I don't know that any entity, college, business, etcetera or individual could ever say that a malware attack will never happen,” said Farlow.

“There's no way to prevent an attack entirely,” Farlow said, “You don't know when it's coming, where it's coming, or how it will potentially attack your systems. What we can do is make sure that we are as prepared as possible for those attacks if they arise as well as we're able to recover more quickly.”
Multi-party authentication tools are being used by COD staff and students to improve their security.
“So whether it's from your cell phone, whether it's from your email address,” Farlow said, “so some of these multi-party authentication systems are in place, and they do significantly add to protecting the systems that you're logging on to.”
COD also has a 5-year Technology Master Plan describing the college’s technology missions, goals, funding, training, also disaster recovery, privacy, and security. It’s posted online on the COD website.
Could a malware ransom attack happen again at College of the Desert? Lumsden says hackers are always finding new ways to exploit the web-based systems students and staff depend on daily. But the key is to be prepared, with the right equipment and procedures in place, and people ready to respond.
Jeff Stahl asked him, “Should it be unnecessary if you’re regularly backing up everything and properly isolating those backups?” Lumsden replied, “Correct. If you’re doing the right things. With the right procedures, policies and backups, you should not have to pay a ransom.”
We’ve asked, but College of the Desert has not yet confirmed if it paid a ransom for the most recent malware attack.
The experts have advice for anyone who uses a computer:
Don’t open links or attachments that you don’t trust, and keep your anti-virus programs up to date.
For businesses of any size trying to improve their computer system security, “One of the best resources out there is cisa.gov,” said Lumsden. “That’s the cyber security and infrastructure security agency cisa.gov.”
Lumsden says the site has tools and tips written for business owners and laymen to understand what they need to do and who they need to talk to bring in experts and help them out.
More important than any technology you can buy is educating the users of any computer system. Lumsden said, “because your users can click a button and work around any technology you have. So educating them on the basics of what to do and keeping it fresh.”

